Mumble is a multi-platform VoIP system that allows us to communicate with a large number of people since the operating system will not be a barrier. By setting up our own server, we will have the guarantee that no one records or stores our conversations. In addition, calls are encrypted using TLS, so if they were intercepted, it would not be possible to access the audio.
We install the Murmur service:
We create the directory where the SSL certificate obtained through ACME will reside:
We install the ACME dependencies:
We install ACME:
We check that the auto-renewal has been crontabbed:
36 0 * * * "/root/.acme.sh"/acme.sh --cron --home "/root/.acme.sh" > /dev/null
We obtain the certificate and define the renew-hook:
[Fri Apr 16 15:49:44 CEST 2021] Using CA: https://acme-v02.api.letsencrypt.org/directory
[Fri Apr 16 15:49:44 CEST 2021] Standalone mode.
[Fri Apr 16 15:49:44 CEST 2021] Single domain='mumble.alfaexploit.com'
[Fri Apr 16 15:49:44 CEST 2021] Getting domain auth token for each domain
[Fri Apr 16 15:49:46 CEST 2021] Getting webroot for domain='mumble.alfaexploit.com'
[Fri Apr 16 15:49:46 CEST 2021] Verifying: mumble.alfaexploit.com
[Fri Apr 16 15:49:46 CEST 2021] Standalone mode server
[Fri Apr 16 15:49:51 CEST 2021] Success
[Fri Apr 16 15:49:51 CEST 2021] Verify finished, start to sign.
[Fri Apr 16 15:49:51 CEST 2021] Lets finalize the order.
[Fri Apr 16 15:49:51 CEST 2021] Le_OrderFinalize='https://acme-v02.api.letsencrypt.org/acme/finalize/118598796/9102581583'
[Fri Apr 16 15:49:52 CEST 2021] Downloading cert.
[Fri Apr 16 15:49:52 CEST 2021] Le_LinkCert='https://acme-v02.api.letsencrypt.org/acme/cert/03b37b765b127029b2e17039601beec8ba42'
[Fri Apr 16 15:49:53 CEST 2021] Cert success.
-----BEGIN CERTIFICATE-----
XXXXXXXXXXXXXXXXXX
-----END CERTIFICATE-----
[Fri Apr 16 15:49:53 CEST 2021] Your cert is in /root/.acme.sh/mumble.alfaexploit.com/mumble.alfaexploit.com.cer
[Fri Apr 16 15:49:53 CEST 2021] Your cert key is in /root/.acme.sh/mumble.alfaexploit.com/mumble.alfaexploit.com.key
[Fri Apr 16 15:49:53 CEST 2021] The intermediate CA cert is in /root/.acme.sh/mumble.alfaexploit.com/ca.cer
[Fri Apr 16 15:49:53 CEST 2021] And the full chain certs is there: /root/.acme.sh/mumble.alfaexploit.com/fullchain.cer
We copy the files to the directory where Murmur expects to find them:
chown -R murmur:murmur /usr/local/etc/murmur/ssl/
We configure the basic parameters of Murmur:
welcometext="<br />Welcome to AlfaExploit Murmur Server</b>.<br />Enjoy your stay!<br />"
serverpassword=PASSWORD
sslCert=/usr/local/etc/murmur/ssl/mumble.alfaexploit.com/fullchain.cer
sslKey=/usr/local/etc/murmur/ssl/mumble.alfaexploit.com/mumble.alfaexploit.com.key
We enable and start the service:
service murmur start
If we use IPFW , we must add the following rules:
# Mumble server:
$cmd 01200 allow all from any to 192.168.69.13 64738 in via $wanif
$cmd 01200 allow all from 192.168.69.13 64738 to any out via $wanif
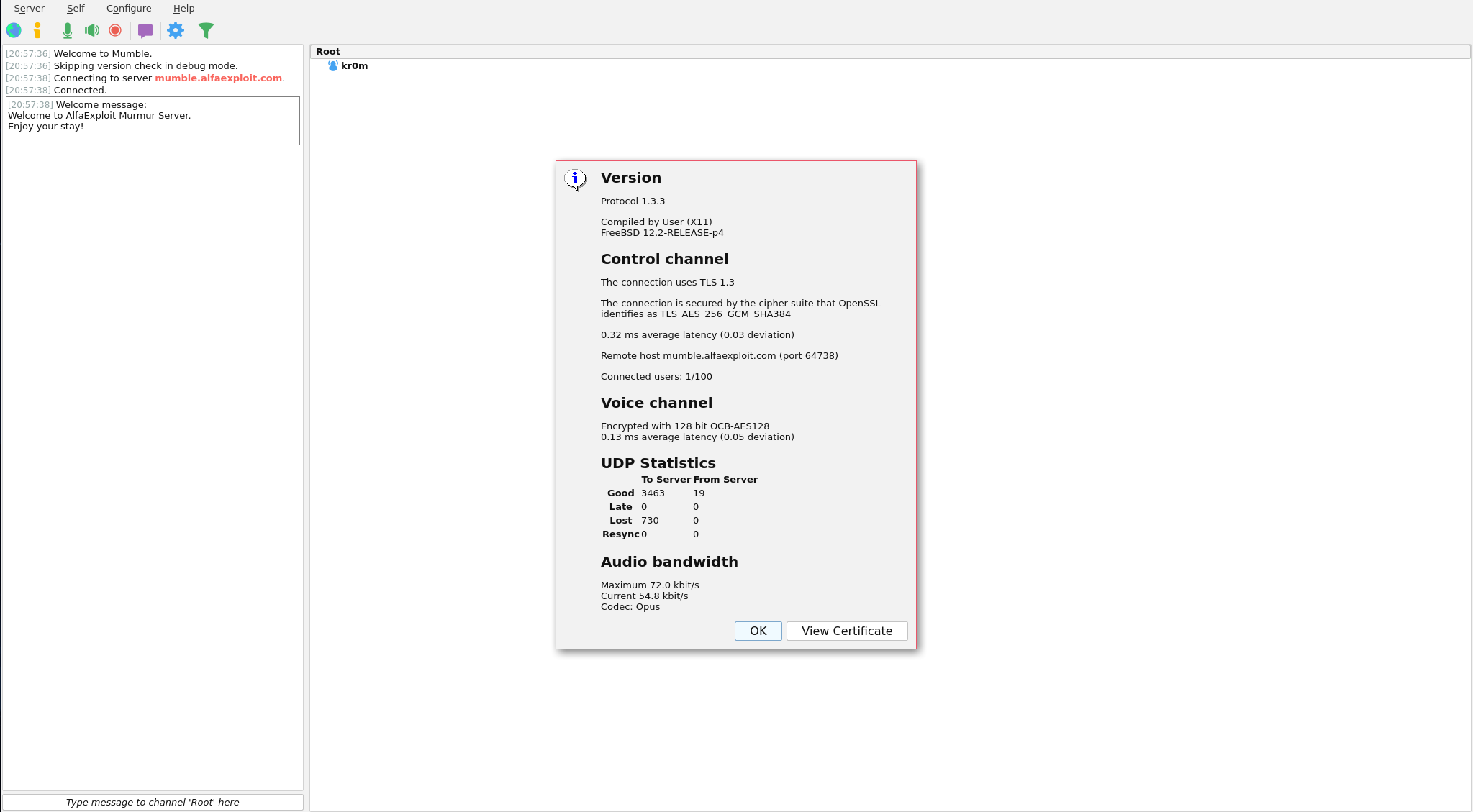
Upon connecting, we will see the banner on the left, and we can also check information about the server: