FreeBSD is a highly flexible and configurable operating system, as demonstrated by its packaging system, whether through binaries or ports. Through binaries, we will save compilation time on old machines and those with few resources, while with ports we will obtain smaller and safer packages since the attack surface on them will be reduced.
Next, I will explain briefly and concisely how to search, install, and update software, as well as how to update the core/base and sources. But before that, we must bear in mind that it is not recommended to mix binary packages with ports since the compilation options of one or the other can be very different and cause problems. If you decide to use a system, you must use it for everything.
- SEARCH
- INSTALLATION
- UPDATE
- UPDATE CORE/KERNEL/SRC
- UPDATE JAILS
- UPDATE ZPOOL
- SECURITY
- CLEANING DOWNLOADED PACKAGES
- REMOVE PACKAGES
- INSTALLED PACKAGES INFORMATION
SEARCH
Binary packages:
The basic command is:
To not show the version of the found packages:
To show the package details:
To search within the descriptions:
Ports:
Before using the ports, we must download the tree, extract it, and generate the index:
We use Git instead of PortSnap because PortSnap only allows us to use HEAD release, while using Git we can choose:
...
origin/2023Q2
origin/2023Q3
origin/HEAD -> origin/main
origin/main
We ensure that we are in the correct one:
main
We can change to any of the available releases using the switch command:
git -C /usr/ports rev-parse --abbrev-ref HEAD
2023Q3
If we want to return to HEAD release that is main:
git -C /usr/ports rev-parse --abbrev-ref HEAD
main
To perform a search:
It is not necessary to search by name, we can do it by any field:
INSTALLATION
Binary packages:
Ports:
We update the ports tree:
cd /usr/ports
make fetchindex
We change to the port directory:
We show the compilation options dialog:
We compile and install:
make install
We remove temporary files in this way to avoid problems when updating to higher versions:
If we want it to ask us all the options before starting the compilation of the port and its dependencies, we must use the config-recursive option:
If we want to know the compilation options of a package, we can consult them:
If we want to reset the options to the ones that came by default:
There is a way to accept the default compilation parameters, very useful for unattended installations:
make install clean
UPDATE
Before updating, it is recommended to create a “boot environment” as described in this article .
UPDATE BASE: CORE/KERNEL/SRC UPDATE
The parts of the OS that freebsd-update will update depend on the configuration indicated in the file /etc/freebsd-update.conf:
Components src world kernel
In this case, it will update the OS source code, core tools, and the kernel.
If we stay within the same version, it will suffice to do:
freebsd-update install
We can schedule the fetch and it will notify us via email if there are updates:
@daily root freebsd-update -t kr0m@alfaexploit.com cron
NOTE: Before moving from one version to another, it is recommended to update as much as possible within the existing version (freebsd-update fetch/install, pkg upgrade).
To move from one version to another, we follow the guide and check the latest RELEASE available.
If it is a minor update, e.g. 12.0 -> 12.1:
freebsd-update install
We restart and finish installing the updates:
freebsd-update install
If it is a major update, e.g. 12.1 -> 13.0, in addition to the steps for a minor update, we must reinstall the binary/ports packages and finish the update.
If we are working with binary packages:
freebsd-update install
If we are working with ports:
cd /usr/ports
make fetchindex
for PORT in $(pkg info|awk '{print$1}'); do PORT_PATH=$(pkg info $PORT|grep Origin|awk '{print$3}') && echo PORT: $PORT - $PORT_PATH && cd /usr/ports/$PORT_PATH && export BATCH="yes" && make clean reinstall clean; done
freebsd-update install
If something goes wrong, we just need to execute the following command to revert the changes:
UPDATE PACKAGES/PORTS
Binary packages:
All binary packages:
pkg autoremove
Ports:
We update the port in question:
cd /usr/ports
make fetchindex
cd /usr/ports/CATEGORY/NAME
make clean
make config
make
make reinstall
All ports:
cd /usr/ports
make fetchindex
for PORT in $(pkg info|awk '{print$1}'); do PORT_PATH=$(pkg info $PORT|grep Origin|awk '{print$3}') && echo PORT: $PORT - $PORT_PATH && cd /usr/ports/$PORT_PATH && export BATCH="yes" && make clean reinstall clean; done
UPDATE JAILS
UPDATE ZPOOL
When we update the OS, it may have made changes to the ZFS version, in which case we must update the ZFS pools we have.
With a status, we can see that the system itself informs us:
pool: zroot
state: ONLINE
status: Some supported features are not enabled on the pool. The pool can
still be used, but some features are unavailable.
action: Enable all features using 'zpool upgrade'. Once this is done,
the pool may no longer be accessible by software that does not support
the features. See zpool-features(5) for details.
config:
NAME STATE READ WRITE CKSUM
zroot ONLINE 0 0 0
vtbd0p4 ONLINE 0 0 0
We upgrade the zpool:
This system supports ZFS pool feature flags.
Enabled the following features on 'zroot':
userobj_accounting
encryption
project_quota
resilver_defer
bookmark_v2
redaction_bookmarks
redacted_datasets
bookmark_written
log_spacemap
livelist
device_rebuild
zstd_compress
draid
Ahora un status ya no muestra ninguna advertencia al respecto:
pool: zroot
state: ONLINE
config:
NAME STATE READ WRITE CKSUM
zroot ONLINE 0 0 0
vtbd0p4 ONLINE 0 0 0
SECURITY
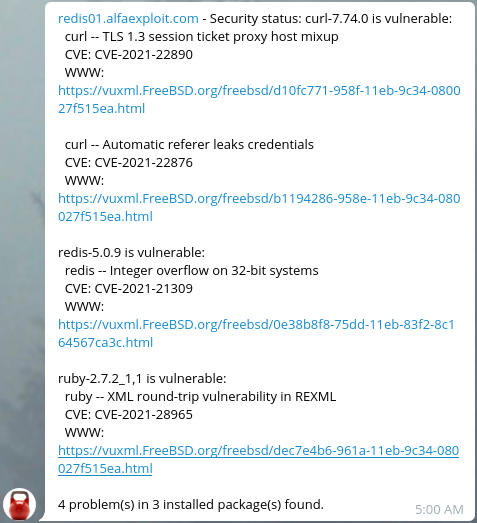
We can check if any of the binary/ports packages installed on the system have any security issues:
A good option would be to schedule a script that sends us a daily Telegram message:
#! /usr/local/bin/bash
function sendTelegram {
message=${@:1}
curl -s -X POST https://api.telegram.org/botAPI_KEY/sendMessage -d chat_id=CHAT_ID -d text="$message"
}
pkg audit -F
SALIDA=$(pkg audit)
sendTelegram "$HOSTNAME - Security status: $SALIDA"
Assign permissions to the script:
The received notifications will look like this:
CLEANING DOWNLOADED PACKAGES
Binary packages:
Ports:
REMOVE PACKAGES
Binary packages:
pkg autoremove
Ports:
make deinstall -> If any application depends on the port, a warning will be displayed
make rmconfig -> Also removes the port configuration
INSTALLED PACKAGES INFORMATION
The following commands are valid for both binary and ports installations:
pkg query -e “%n=NAME” “%n-%v %Ok %Ov”