In most cases, IPMI/KVM access is restricted to an internal management network to provide better protection than exposing it publicly. However, the downside is that it makes it difficult to access in case of an emergency. In this article, we will see how to tunnel traffic through an SSH connection, allowing us direct access to the KVM of the private network.
It seems that each KVM opens different ports for its operation, so first we will find out the correct ports by scanning with Nmap. We do this from the intermediate jump host:
Starting Nmap 7.80 ( https://nmap.org ) at 2021-04-16 22:05 UTC
Nmap scan report for IP_LAN_KVM
Host is up (0.0012s latency).
Not shown: 65523 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
443/tcp open https
623/tcp open oob-ws-http
5120/tcp open barracuda-bbs
5123/tcp open unknown
5124/tcp open unknown
5127/tcp open unknown
5988/tcp open wbem-http
7578/tcp open unknown
7582/tcp open unknown
50000/tcp open ibm-db2
Nmap done: 1 IP address (1 host up) scanned in 6.22 seconds
Now that we know which ports we want to tunnel, we proceed to do so. As root on our PC, we execute:
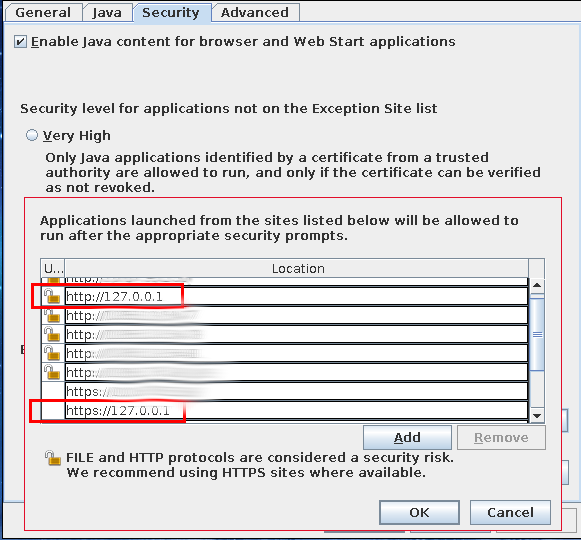
We add the loopback IP to the Java exception list:
https://127.0.0.1
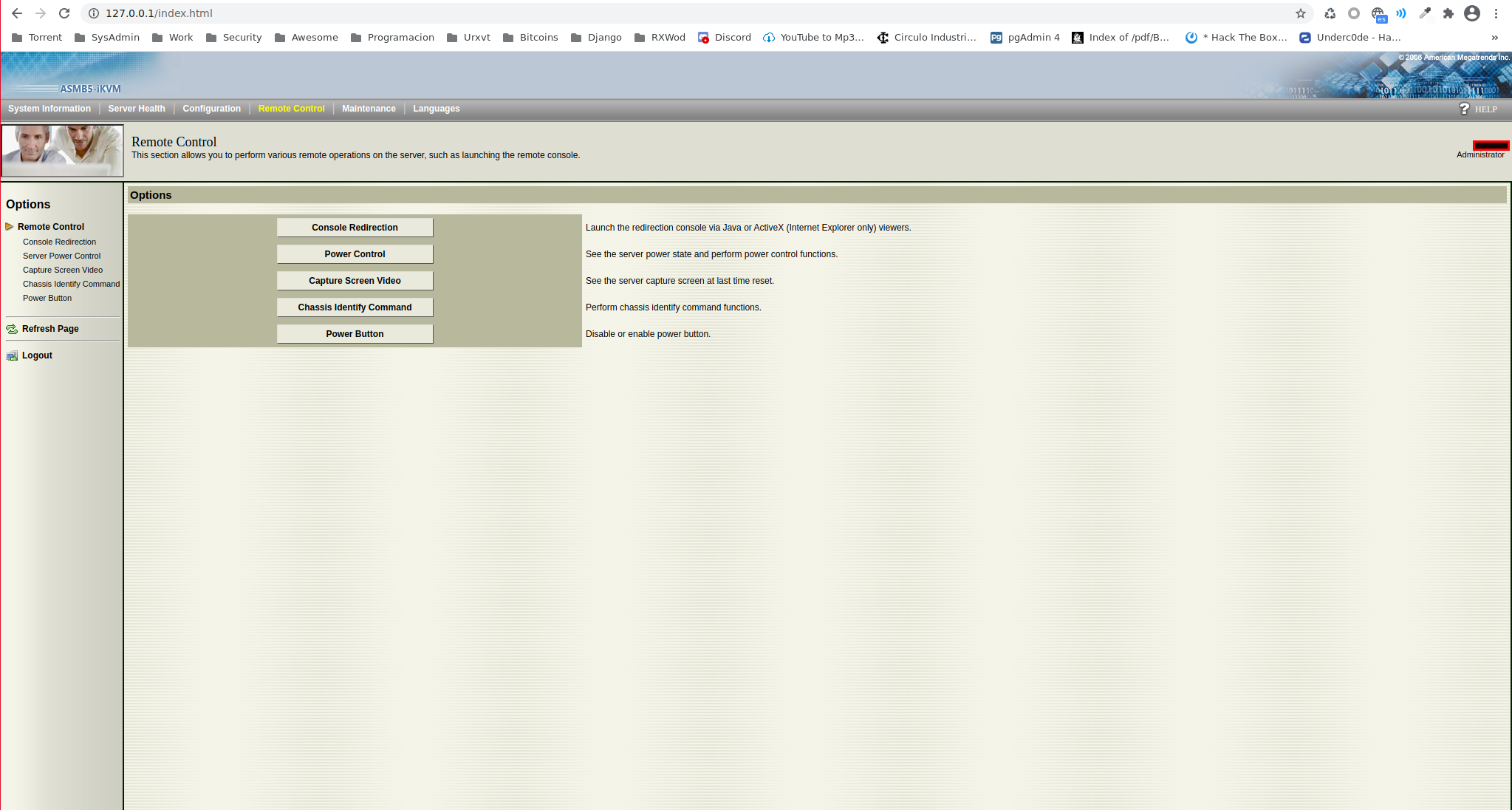
Now we can access the web interface to download the Java applet. From Chrome, we can log in to the web interface:
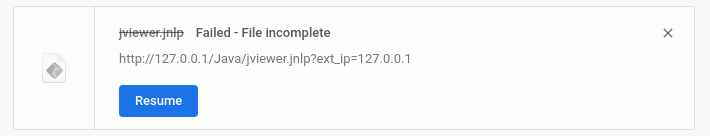
But when downloading the applet, the following error appears for some unknown reason:
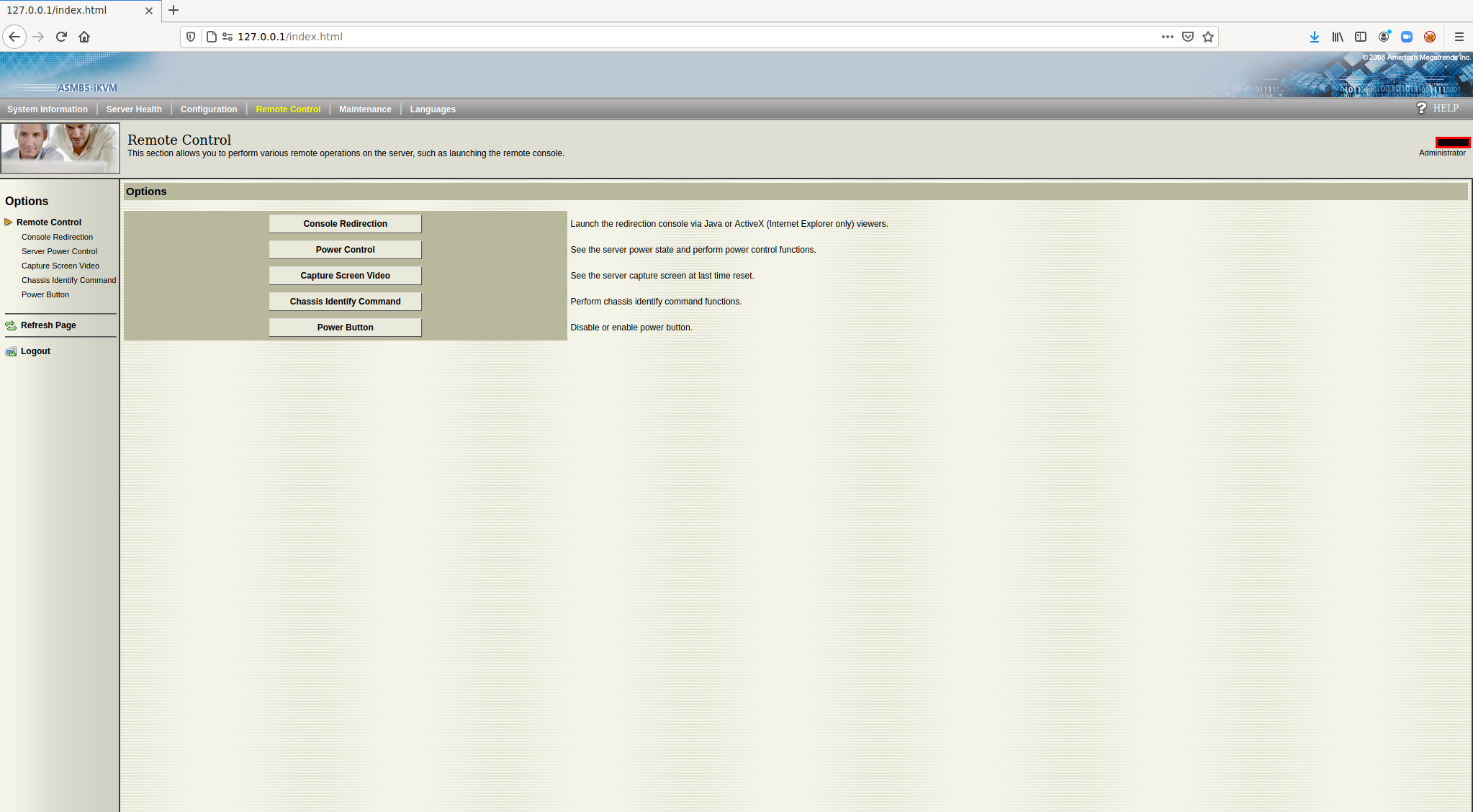
However, Firefox does not have any problems:
Now that we have the jnlp file, we launch it with the script from
this previous article
:
In the following screenshot, we can see the Java applet starting from a Gentoo ISO:
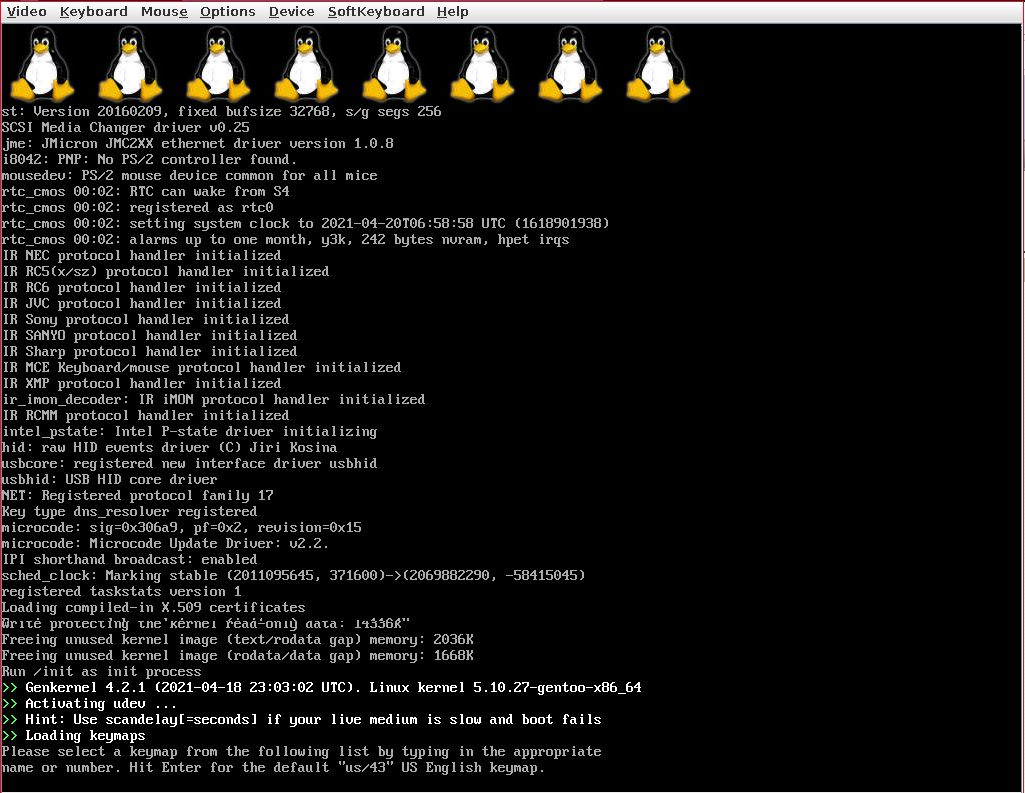
Surely, through tools like sshuttle, the process could be a little more transparent, but it seems that sshuttle has some problems in FreeBSD, so I have opted for the most generic approach, Ssh. Another option would be to install a VPN, but the fastest way is to use Ssh since no additional service needs to be installed.