Besides allowing us to securely access our servers, SSH provides us with very interesting tunneling functionalities, especially when working in highly restricted environments.
All these tunneling topics may seem more or less useful, but knowing them can help us in certain cases when the network is not working properly by passing traffic through another device or for specific cases where it is not worth modifying the FW rules just to perform an isolated operation.
We can set up direct and reverse tunnels.
Direct tunnel:
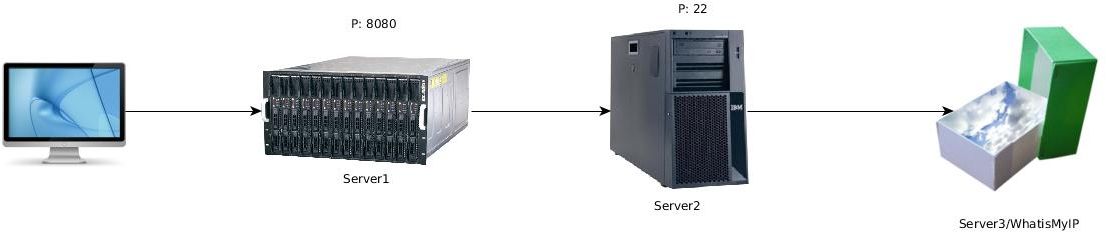
We will execute the command on Server1, and we will check the correct operation from PC.
The way to set up the tunnel is:
In our example, we will use
www.whatismyip.com
as Server3, so we can check that the public IP is that of Server2 ;)
www.whatismyip.com. 240 IN A 141.101.120.14
We connect to Server1:
ssh -L 8080:141.101.120.14:80 -A -g root@Server2 –> It will ask for Server2’s password
In PC:
http://Server1:8080 --> Server2's IP will appear
What has happened is that we have connected to Server1:8080, which sends the traffic to Server2 through port 22, and from there it forwards it to 141.101.120.14:80
Let’s imagine that we don’t want to use Server2, but we simply want to tunnel the traffic through Server1:
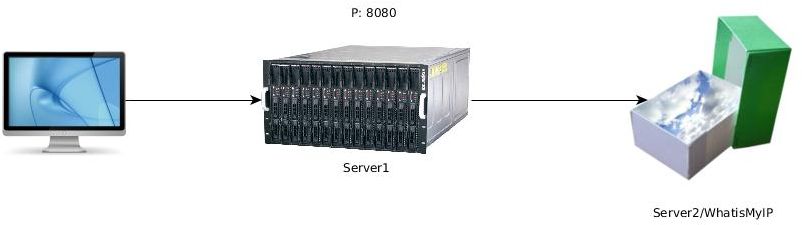
In this case, www.whatismyip.com will be Server2.
We connect to Server1:
ssh -L 8080:141.101.120.14:80 -A -g root@localhost –> It will ask for Server1’s password
In PC:
http://Server1:8080 --> Server1 IP
This way we can mask our IP behind another server either for privacy reasons or due to firewall restrictions on the final server ;)
Reverse tunnel:
This type of tunnel will allow us to connect to servers where we don’t have SSH access, for example when we are given access through teamviewer or some other similar software, the idea is to initiate the connection from this server to an external one and then recover this connection, a real crack move ;)
We connect to Server2 (teamviewer):

We connect to Server1:
ssh localhost -p 8080 –> Boom, we have a nice SSH shell on Server2!!
We can leave the following script in the cron of our remote server:
#! /bin/bash
N=$(ps aux|grep 'ssh -nNT -R 4000:localhost:22 root@www.alfaexploit.com'|grep -v grep|wc -l)
#echo -e "N: $N"
if [ $N -lt 1 ]; then
#echo -e "-- Starting reverse tunnel"
ssh -nNT -R 4000:localhost:22 root@www.alfaexploit.com &
#echo -e "++ Done"
fi
This way, if the tunnel goes down, it will be available again in a minute ;)
All these tunneling topics may seem more or less useful, but knowing them can help us in certain cases when the network is not working properly by passing the traffic through another device or for specific cases where it is not worth modifying the FW rules just to perform an isolated operation.